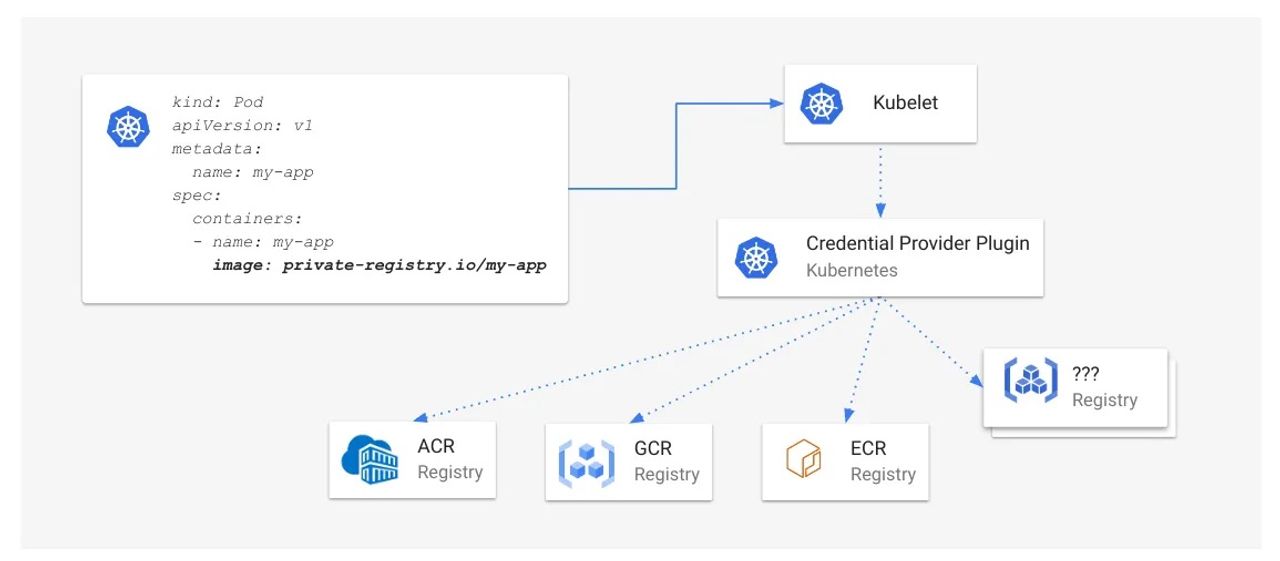
This post will give you and overview on how docker performs the authentication into image registries, and how changes to the credentials alters the workflow when multiple nodes are involved.
The first part of this post gives and overview of what docker is, where docker images are stored and what docker login does. If you already know some basics on how Docker and Docker Swarm works, you can skip directly here.
Docker has a client-server architecture and most of the docker commands are communicating with the docker daemon via some REST-ish API.
[…]